Securing your ELK stack - setting ElasticSearch, Kibana and Logstash security
In my previous post, I’ve shown a way to expose Kibana (ELK) instance to the internet using Nginx. This helps us hide our internal infrastructure behind a secure gateway reverse proxy. This, however, doesn’t mean that the actual Elastic Stack is secure. To do this, we need to configure the security settings for the cluster and related supporting applications. In this article, I will show how to do exactly this.
Naturally, these settings are added to your configuration files, like elasticsearch.yml, logstash.yml or kibana.yml.
Since I am using Docker, from now on I will be showing how to set up these settings using environmental variables in Docker or Kubernetes containers.
Setting up Kibana in a subpath and Nginx reverse proxy
Have you tried to set up Kibana in a subpath just to be met by the error {"statusCode":404,"error":"Not Found","message":"Not Found"}?
Or maybe you want to secure your infrastructure using Nginx reverse proxy.
I will show you how to do these two things at the same time.
I’ve written this guide, because the information found here, was scattered through many pages and takes time to find out and test.
Setting the Nginx reverse proxy
There’s not much to it, just add the following snippet to your configuration:
1 | location ~ /kibana { |
Tgus tells Nginx to redirect all the traffic coming to the /kibana subpath to your Kibana server.
Setting Kibana
Now, there are two ways to set Kibana - environmental variables, when using a Docker container or through the kibana.yml.
Since I’m using Docker, let me start with this one.
1 | kibana: |
The two important things here are SERVER_BASEPATH, which tells Kibana to server its pages from /kibana instead of /, andSERVER_REWRITEBASEPATH, which tells Kibana to handle rewriting of page and API URL requests coming under the /kibana subpath.
You can set your server to do this, but using the Kibana setting is a lot easier, most of the time.
In the yml file, these two settings are called:
1 | server.basePath |
That’s it! I hope this saved you some time.
Additiopnal consideration
If you’re planning to expose your Kibana app to the internet, through reverse proxy, make sure you have the proper security configuration in place.
Inspiration:
https://serverfault.com/questions/775958/reverse-proxy-for-nginx-configuration-for-subpath
https://discuss.elastic.co/t/kibana-and-nginx-in-subpath/90280/5
https://www.elastic.co/guide/en/kibana/master/settings.html#server-rewriteBasePath
https://stackoverflow.com/questions/17423414/nginx-proxy-pass-subpaths-not-redirected
https://forum.chirpstack.io/t/running-application-behind-reverse-proxy-with-subpath/7057
Firefox 63 security warning issue
The latest version of the Mozilla foundation browser - Firefox Quantum 63.0, introduces an issue with some websites, where even though there is a valid security certificate, it doesn’t load the page. The below image shows a website that i usually access using Firefox. Other browsers like Edge and Chrome validate the certificate correctly and display the page.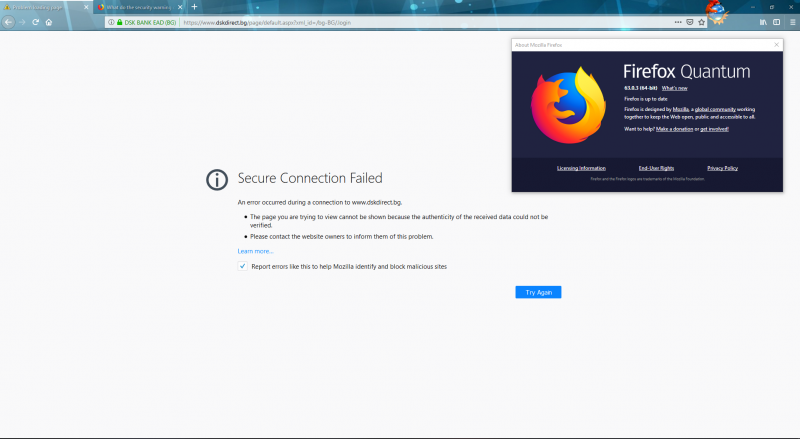
Previously there was an option to add an exception and continue to the site anyway (which is also described on the help page), but in this situation it doesn’t exist, probably because the certificate is found as valid. While i do not know the source of this issue, the fix is very simple if you encounter it - click on the shield icon in front of the URL and “Clear Cookies and Site Data”. In the popup click OK after verifying the domain name - this will clear all temporary data in your browser for this website and open it clean, the next time you load the page.