
To protect your application with a Single Sign-On (SSO), there are several things that you need to configure. One of them is the so-called Identity Provider (IDP).
Okta is a widely used enterprise identity provider. In this guide, I will show you how to create a developer’s account with Okta and start using their services with a test Open ID Connect (OIDC) application.
Here are the steps
Visit https://developer.okta.com/signup/ and sign up for an account
You will receive an email for account confirmation and setting password
Set your password
You will be redirected to your own SSO Domain which looks like this https://dev-some_random_number-admin.okta.com/admin/dashboard
From the left menu, choose
Applications > Applications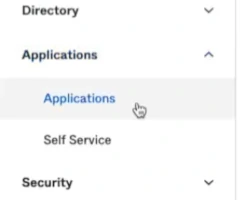
Click on
Create App Integration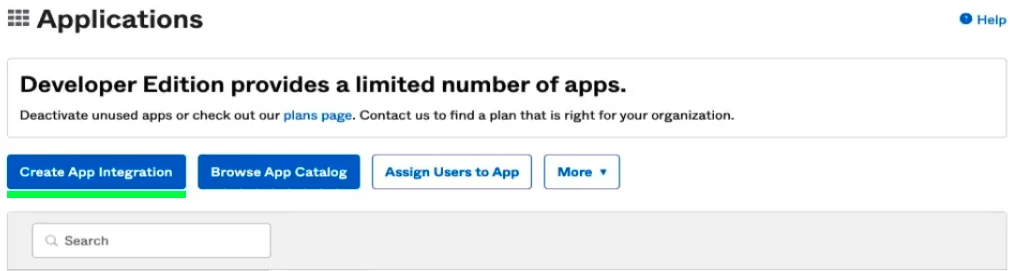
Choose
OIDCAnother section, called “Application Type”, will show in the dialog. Choose
Web Application.
You will be redirected to another page, where you will have to fill the application details.
Fill your application name in the
App integration namefield - this can be anything you like, as it is only for your convenience, when using the Okta dashboard.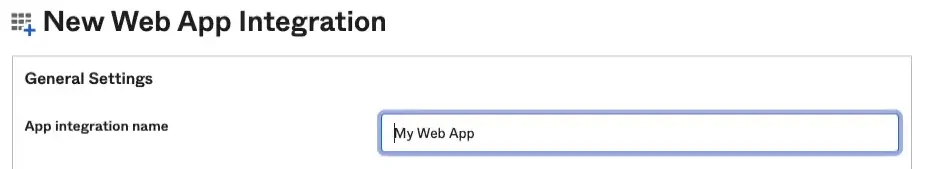
Scroll down to
Assignmentsand selectAllow everyone in your organization to access.
As the setting suggests, everyone registered with your Okta domain will have access to this application. We can further control the access to different application in the domain, using groups or directly by account, but this is out of scope for this guide.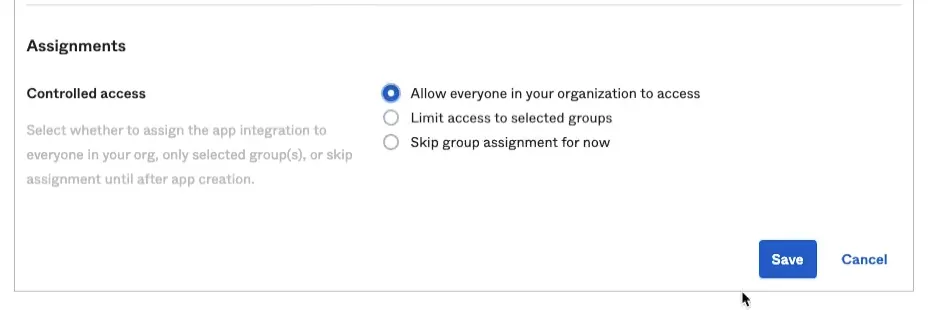
Saveand you’re done.(Additional steps) Configure your application to use the SSO settings that can be found in the
GeneralandSign Onsections of your application’s dashboard.For information on how to do this:
- Check my article on “Protecting your application with Nginx and Vouch proxy”
- Check out this example on GitHub
Comments